
FBI Warns Businesses Of Cyber Attack From China
Who Has Been Impacted by Chinese Cyber Attacks? At the beginning of the year, the FBI warned businesses to protect themselves from cyber attacks by[...]

How Does Outsourcing IT Help Fuel Business Growth?
You already know what IT stands for: information technology. What you might not know is that most companies have a pretty poor grasp of how best to[...]

How To Add A Column From an Example In Microsoft Excel
Microsoft Excel has been around for ages. However, did you know that there are a whole host of functionality features to simplify your workflow and[...]

What Should Be In Your 2019 Technology Strategic Plan
Making an Ultimate Technology Plan for the New Year Times are changing. Apparently, this is the case considering we’re about to head into 2019. How[...]

9 New Game-Changing Additions To Microsoft Office 365
Microsoft recently announced several new updates to Office 365. These updates and additions will help organizations who want to streamline efficiencies and remain compliant with[...]
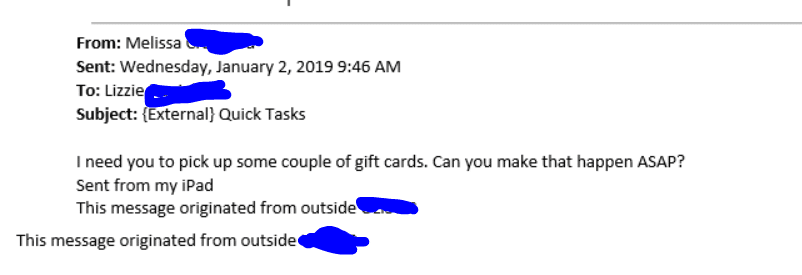
SCAM ALERT: Google Play Gift Cards
If there’s a will there’s a way when it comes to scammers, especially with gift cards. Everyone loves gift cards. Consumers love how easy it is to[...]

World Braille Day
On January 4th, 1809, Louis Braille was born. Louis Braille was a child who lost his vision in an incident involving a sharp tool at[...]

Should Your Business Upgrade It’s Website To WordPress 5.0.2
Only a few short weeks ago, we wrote about the introduction of WordPress 5.0 in early December and discussed whether or not your company should[...]

5 Extremely Important Facts Every Small Business Owner Needs To Know About Managed IT Services
As small business owners rely on IT more than ever before, a growing number are turning to managed service providers to obtain the high-tech IT[...]